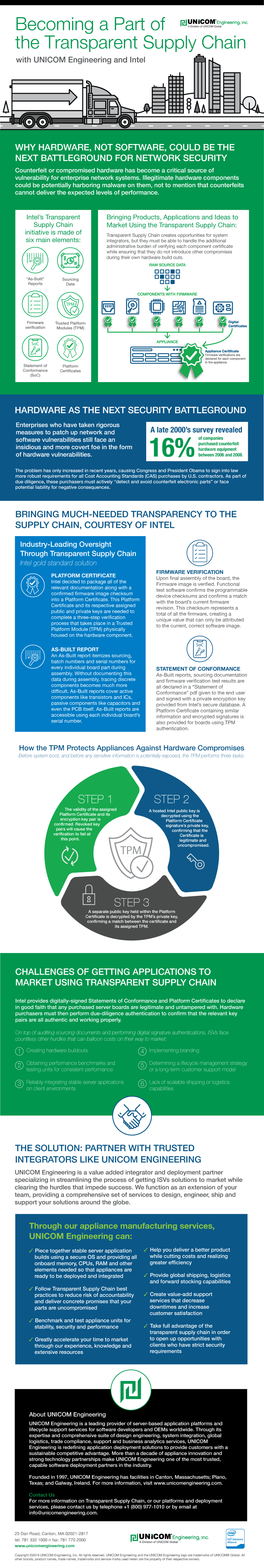
Increasingly, enterprises are demanding transparent supply chains as a way to prevent counterfeit components from creating vulnerabilities within networks or systems. Incidents like the recent revelation that Apple may have purchased compromised motherboards are the reason that sourcing information and verification of supply chain integrity are becoming mandatory for certain contracts. The U.S. Government, for instance, demands proof of such oversight for many of their DFARS and Cost Accounting Standards (CaS) contracts.
To solve this problem, Intel has developed the Transparent Supply Chain initiative. It provides several levels of authentication, including the possibility of installing a Trusted Platform Module (TPM) directly onto hardware components that perform their own encryption checks as authentication. Other assurance like as-built reports, digital certificates and extensive sourcing data provide the confidence contractors, suppliers, OEMs and ISVs need to confirm that their parts are legitimate and untampered with from the originating source.
UNICOM Engineering can partner with solutions developers to help them take advantage of Transparent Supply Chain products while conforming with any new hardware-side standards needed for compliance and integration.
Learn More About the Transparent Supply Chain and How UNICOM Engineering Can Help
Take a look at our infographic below to learn more about how the Transparent Supply Chain can provide peace of mind and what your company can do to participate in it. For more in-depth information, you can also read our whitepaper: “Becoming a Part of the Transparent Supply Chain” by downloading it from the link below.