Getting an industry-specific solution to market requires the skillful manipulation of time, money, and resources to produce the most competitive solution as quickly as possible, all while maximizing revenue.
We start with scalable and reliable hardware you can trust combined with a flexible engagement model built to adapt and scale as your business grows – all designed to maximize the value of your resources, enabling growth while controlling costs.
Demand for Security Appliances are on the Rise
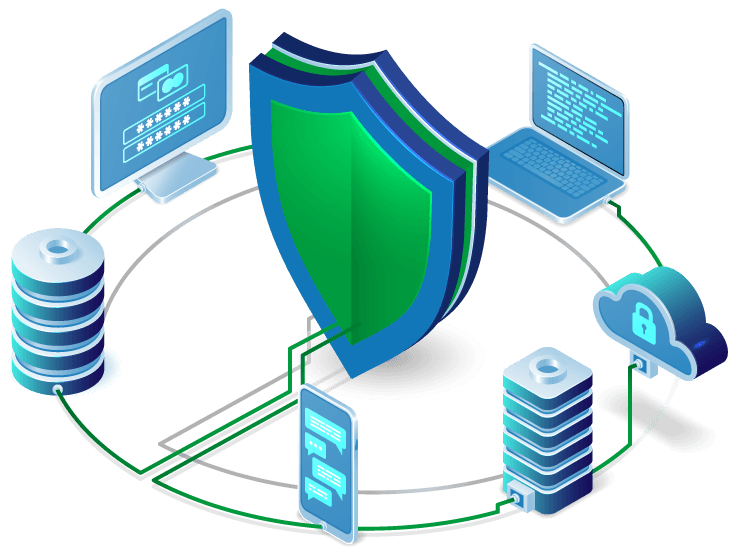
Information Security
Security threats are a constant concern as incidents and breaches escalate, and attacks become more targeted. The rise in threat vectors has compounded the issue with data sharing across networks, the internet, mobile devices, the cloud, and social networking outlets.
The Need for Data Storage Solutions Continues Rising
Data Storage Solutions
We as consumers store, view, retrieve, analyze and share massive amounts of data every minute of every day. This combined with trends like IoT that will capture massive amounts of data to deliver new conveniences and information to consumers will only drive the need for storage capacity to its limits.
The New Age of Telecommunication Equipment Solutions
Telecommunications
Communications today is defined in texts, videos, posts, tweets, blogs, calls, etc. and the lines between our home and work lives have blurred as our activities converge on our devices.
Answering the Demand for Digital Media Platforms
Digital Media
The digital media market is exploding with vast amounts of ultra-dynamic content, connected devices, and customers wanting rich media delivered to any screen they choose at a moment’s notice. This environment has given rise to solutions geared towards every aspect of the digital value chain.
The Growth in Healthcare IT Solutions
Healthcare IT
The Healthcare industry has undergone significant change in the way that patient information is gathered, stored and retrieved. Healthcare IT solutions have enabled the industry to leverage technology to better manage this data resulting in time and cost savings while increasing the overall quality of care provided.
Computing Environments Built for Scale, Flexibility and Performance
Hybrid Cloud
Cloud computing has revolutionized the modern enterprise by enabling organizations to reinvent the ways they operate by bringing cloud capabilities of Microsoft Azure to on-premises data centers. This paved the way for a hybrid approach that merges the two using both public and private per the needs of the application, cost, and security requirements.
Industry Resources

Article
How 2nd Gen Intel® Xeon® Scalable processors can power disruption
Artificial Intelligence is changing how we see the world and solve problems

Article
Storage dilemmas have been around for years slowing down critical operations
What happens when you pair Intel's new class of memory with its 2nd Gen Xeon® Scalable processors?
Discover Why Leading Technology Companies Trust UNICOM Engineering
The quicker we start to engage, the faster this can happen. We’ve provided some baseline information above, but we are more engaging in person. Let’s discuss the technology and services that optimize your application and drive performance.